Anti-Virus software from Bitdefender
Block and mitigate online threats


1CS is an authorized reseller of Bitdefender Anti-Virus Solution
Why SMB’s choose Bitdefender Anti-Virus/Anti-Malware Solution over the others
Consistently the best security suite
500 million endpoints protected
Easy deployment from 1CS
Powerful but light
Combined anti-virus and anti-malware
Bitdefender’s machine learning algorithms, security capabilities and extensive worldwide coverage stop even the most sophisticated ransomware and detect zero-day attacks in real time.
Simple but effective IT security tools every business should deploy:
Content Control
Bitdefender can restrict URLs by class, be easily adjusted and timed to meet the needs of the individual users.
Device Controls
Select the kind of device or specific devices that are allowed to operate on your network, and which require action.
Advanced anti-exploit
Bitdefender defends against both known & unknown exploits as well as zero-day threats by focusing on methodology.
Process Monitoring
Process inspector monitors running processes for suspicious behaviour 24/7, resulting in immediate protection.
Combined AV and AM
Bitdefender is a two-in-one protection solution that includes both anti-virus and anti-malware technology.
Optional Add-ons
Bitdefender supplies numerous security add-ons which cater to the demands of various enterprises.
No anti-virus catches more threats and has fewer false positives than Bitdefender, which makes it a highly recommended security tool for SMBs
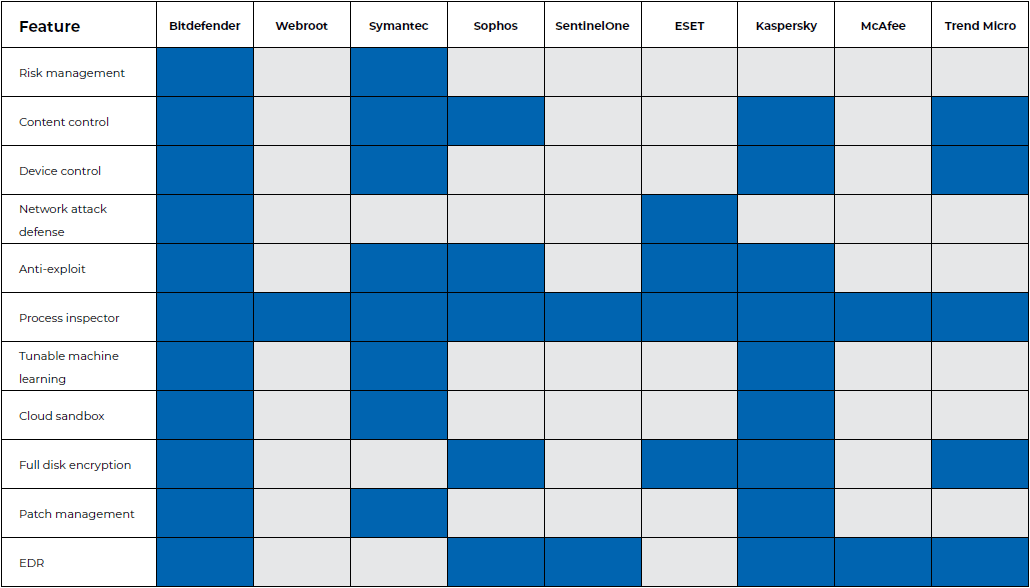
Comparison of Bitdefender features to that of leading competitors
For more information:
Competitive analsyis of Bitdefender vs top rivals
| Feature | Pain-points | Bitdefender differentiator | |
| 1. |
Anti-virus &
|
Businesses seek new anti-virus and/or endpoint security mechanisms when they’re displeased with their existing products’ performance (for example, low protection rates or inefficient navigability) or want to expand their security posture. | • Top rankings from independent testing. • Easy to use, recurring usage-based subscription within a single cloud web console and boasting integrations with all major PSA and RMM, ensuring automation of security operations. • Additional layers of security, such as risk management, content control, exploit defence, and network defence, reduce expenses and attack surface area. |
|
2.
|
Advanced threat security |
Fileless protection and cloud sandboxing aren’t available from every vendor, and only a handful offer configurable machine learning. | • Contains an all-in-one, cost-effective solution for defending against sophisticated assaults. • Advanced ransomware, fileless assaults, and other dangers are all prevented via customizable machine learning. • Cloud-hosted sandboxing with automatic and human submissions, offering enhanced analysis, threat-context, and visibility. • Proven success in blocking PowerShell and other script-based assaults. |
|
3.
|
Security for virtualized environments |
Lack of efficiency in the detection of threats and/or the use of excessive resources by businesses and security providers has a negative impact on both the company’s bottom line and the experience of its users. | • Unlike competing systems, it works on any hypervisor or cloud environment. • Improved virtual machine detection and security without sacrificing security. • According to testing using independent benchmarking tools like LoginVSI, virtualized desktops or servers have the best performance. |
|
4.
|
Patch management |
For Windows patching, SMBs commonly deploy a variety of applications. They may deploy specific tools for third-party patching, however due to the slowness of such tools, they frequently lag behind. | • Simple manual and automatic vulnerability patching, including scanning, scheduling, reporting, and the ability to delay reboots. • Fastest scanning capabilities for missing patches, using complete and prioritized information. • Largest database of third party security and non-security patches for Windows operating systems. |
|
5.
|
Full disk encryption |
Many SMBs commonly store encryption keys manually to save money and utilise different providers for various security solutions such as endpoint security. | • Native encryption methods, such as BitLocker for Windows and FileVault for Mac, avoid performance and capability concerns. • Produces encryption reports in order to keep track of policy implementation and demonstrate compliance. • Provides features for maintaining and recovering encryption keys, as well as centrally managed encryption with pre-boot authentication. |
|
6.
|
Endpoint detection & response – EDR |
Although specialized EDR suppliers provide sophisticated tools, many of them are also more difficult to use. Other rivals simply do not provide EDR capabilities or solutions that are antivirus-integrated. | • Detailed visualisations of security holes and incidents. • Anomaly defence establishes user behaviour baselines in order to detect variations and compromises. • Provides automatic or one-click replies as well as simple attack descriptions. • Combines data from numerous sensors to generate simple alerts for potential assaults. |
| 7. | Overall differentiator |
Intentionally left blank. | With one single console and agent for antivirus, antimalware, and endpoint protection, adding Bitdefender to your security stack allows you to simplify security, enhance performance, and lower costs. |
The cost of protecting your devices
Bitdefender
per device- Standalone anti-virus
Managed Bitdefender
per device- We manage the anti-virus solution


